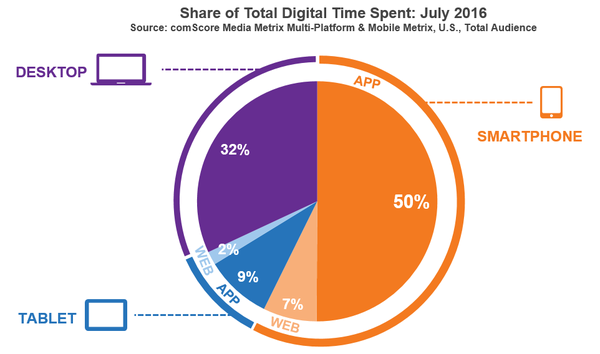
There is no denying the value and popularity of mobile devices. Smartphone apps now account for 50% of all time spent online, and 68% of that online time was spent on a mobile device.
(graph curtesy of comscore.com)
With increased usage comes increased risks. We know the basic dos and don’ts for business security, but where do mobile devices come into play? A recent Tech Pro Research survey of “chief information officers, technology executives, and IT employees” showed that 45% of the employees believed mobile devices to be a weak spot in their company’s security. According to the same survey, “47% of respondents reported that almost all employees at their company used either company-provided or personal devices for work purposes.” Security breaches like the one at Yahoo, believed to be the largest breach ever publicly disclosed by a company, remind us that no matter where information is stored, it is not safe from harm. This is especially dangerous for small businesses, because security breaches could lead to “mistrust between provider and customer.” With that in mind, here are some of the biggest mobile device security threats and how to protect your business from them:
Unsecure devices
Many users do not take basic security measures, like locking their phones, backing up data, or downloading an app allowing them to locate their phone or remotely erase data, should their device go missing. 64% of users did not use a lock screen at all. Using a password or PIN on your lock screen is a simple measure you can take to make your device more secure.
Malicious Software and Mobile Operating Systems
Both Android and iOS users are susceptible to malware and other malicious software. Android phishing and ransomware try to trick users into giving up their information. A new Android phishing Trojan, for example, attempts to fool users into giving their bank credentials by using a fake pop-up screen over the bank’s real login page. Though Apple tightly controls what apps are sold in its app store, iOS is also still vulnerable. Bootlegged developer software like XcodeGhost began to show up in Apple apps in 2015, along with other types of malware.
Both Apple and Google are working to fix security vulnerabilities, but the speed at which manufacturers relay patches can vary, so always download updates on your mobile device as soon as possible. Be sure not to root or jailbreak your phone, as this leaves them more vulnerable to attacks.
For extra protection, Antivirus apps like McAfee, AVG, and Lookout are also available in both the Apple app store and Google Play store.
Lack of Employee Education
Many vulnerabilities and attacks are a result of lack of awareness. Make sure your employees are aware of safety best practices to protect company data, such as:
- Using two-factor authorization
- Using auto-locks and passwords on home screens
- Backing up data to the cloud
- Using caution when downloading apps and opening emails
- Using lock codes for apps and vault apps for an extra layer of security
Ensure that upper level executives understand how great of a threat security breaches can be. If necessary, outsource your IT. It is difficult for one IT professional to monitor the security for an entire company or organization, and this could lead to vulnerability.
As mobile device usage increases, attackers become more sophisticated. Be sure to include mobile devices in your company’s daily security efforts.
