In today’s ever changing landscape of Malware and network threats, visibility and control of protocols and applications, is a key element in providing a robust and manageable security posture for any organization. Cisco FirePOWER and AMP technology enables visibility and context based security across the whole network. Advanced Malware Protection or AMP for short, couples with big data analytics with a single pane of glass for management, discovering threats and keeping track of files as they are downloaded from the net or discovered on endpoints.
Cisco’s approach to network security involves three main phases - Before, During and After. We’ll touch on each of these phases in this post. It’s important to understand where each security product fits in this view of network threats so we can better prepare and defend our networks.
Why use Cisco FirePOWER?
Traditional firewalls fall short in discovery of advanced threats. IPS can only match against known attack signatures and typically increase false positives and as a consequence burden IT and network security staff. Cisco’s Next-Generation Firewall and IPS solutions armed with Advanced Malware Protection minimize the typical “background noise” associated with running a standard IPS. By discovering the end-point, its operating system and applications, as well as associating a user account with session info, Cisco FireSIGHT (the management center for FirePOWER) is able to wrap context around your network. Providing a detailed view of current applications, their business relevance and risk as well as identifying and blocking known threats and alerting on suspect behavior. One of the benefits to FirePOWER is the use of Impact Flags and Indicators of Compromise. These are two high-level alerts which allow IT staff to focus only on those systems exhibiting anomalous or malicious behavior, rather than letting a serious alert go by being lost in the noise of an average network. Because FirePOWER is contextually aware of the systems it is monitoring, it is able to associate relevant threats to your environment. For instance, why load signatures into your IPS for Linux if you are a 100% Microsoft shop? FirePOWER will learn your network and can make recommendations as to what signature bases to load based on what it sees.
So what’s securing the network before an attack?
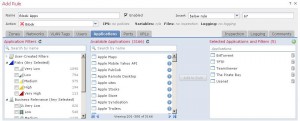
People typically only consider the perimeter firewall as the main point of entry to a network when evaluating network security. Traditionally this has been a valid approach since the front door to the Internet is the only means an attacker might have to leverage their way in. As we’ve seen in recent breaches however an attacker doesn’t necessarily need a misconfigured firewall rule or unpatched server to let them in. Malware sites, Java and Flash exploits, Phishing campaigns even Social Engineering are often used to gain a foothold into an organization, exploit is just one innocent mouse click away for an unsuspecting end user. Application Control is key in minimizing attack surface. Suppose there is no legitimate reason to permit BitTorrent and Tor Browser traffic through the network. One approach would be to drop such applications thus minimizing the attack surface. Cisco FirePOWER can block specific applications, or take a very broad-brush approach to drop low business relevance, high risk categorized applications at the edge. There are over 3,100 applications and protocols that can be identified and controlled. Granular controls can be used to make exceptions if necessary. For instance if only users in the IT group should be allowed to use specific protocols like FTP, RDP, SSH - but those same applications should be blocked for all non-IT users. Using Cisco FirePOWER that rule would be very straight forward to create, no special CLI skills required. Maybe you don’t do any business overseas, Cisco FirePOWER can block specific countries or whole continents from communicating over the network. Using a Cisco maintained Geo-Database, stay on top of the constant IPv4 address space fragmentation and block before the breach. Of course using a strong perimeter firewall like the trusted Cisco ASA platform and secure remote access with Cisco AnyConnect are also crucial in providing security before an attack.
What about during an attack?
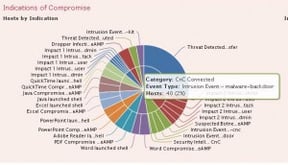
Cisco FirePOWER with Intrusion Prevention based on industry leading SourceFire Snort technology keeps a watchful eye on network traffic while checking for and blocking known attacks against vital resources. If an internal user happens to be tricked into clicking a link that redirects them to a site located behind an IP address with a bad reputation, how could we stop this? Using pre-determined lists of known BotNet, CnC, Malware and Phishing sites we block all attempts inbound or outbound, with Security Intelligence lists maintained by Cisco’s global security team. If a user downloads an office document or other file that’s been infected, how could we prevent the spread of malware? Cisco AMP for network, and AMP for Endpoint is uniquely positioned product capable of performing file hashing and cloud lookup in real-time. Rather than sending an entire file out for analysis, AMP collects and uploads the SHA256 hash (think of it as a finger print) for files that cross the FirePOWER sensor. By using this very efficient method, a quick decision can be made about any given file. If the SHA256 matches a known malicious file the sensor can cut the user off from the download automatically. Suspect files can also be collected for offline analysis and sandboxing if the administrator chooses to do so. AMP doesn’t replace traditional AV, but rather augments these solutions and provides another layer of intelligence and control.
And after we’ve been breached?
Unfortunately, the question is not if a breach will occur,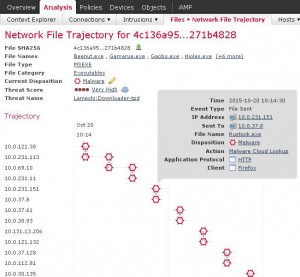 but when. Industry statistics show that on average when a breach occurs it will go on undetected for 229 days before it’s discovered and remediation can begin. The prevalence of zero-day exploits being used means traditional security products fall short of detecting and preventing these threats not yet discovered in the wild. Cisco AMP however can send alerts retrospectively, bringing attention to files that have already been passed through to the end user. By sampling the SHA256 and storing that information, when a file is later found to contain malicious code Cisco publishes an update and that information pulled in to each customer’s FireSIGHT Management Center. The history of who downloaded a given file and when, what endpoints it has moved between, what new file names and processes the Malware has spawned all can be tracked. This level of visibility and intelligence is crucial in speeding up the time to fully remediate systems, by allowing IT staff to target only those computers involved in an infection, rather than scrambling to scan and scrub every PC in the company. Cisco AMP for Endpoint can also assist in remediation, as well by pushing out a custom blocking policy from the Cisco AMP console.
but when. Industry statistics show that on average when a breach occurs it will go on undetected for 229 days before it’s discovered and remediation can begin. The prevalence of zero-day exploits being used means traditional security products fall short of detecting and preventing these threats not yet discovered in the wild. Cisco AMP however can send alerts retrospectively, bringing attention to files that have already been passed through to the end user. By sampling the SHA256 and storing that information, when a file is later found to contain malicious code Cisco publishes an update and that information pulled in to each customer’s FireSIGHT Management Center. The history of who downloaded a given file and when, what endpoints it has moved between, what new file names and processes the Malware has spawned all can be tracked. This level of visibility and intelligence is crucial in speeding up the time to fully remediate systems, by allowing IT staff to target only those computers involved in an infection, rather than scrambling to scan and scrub every PC in the company. Cisco AMP for Endpoint can also assist in remediation, as well by pushing out a custom blocking policy from the Cisco AMP console.
In closing
What about deployment and sizing for my specific environment? Cisco FirePOWER has many deployment options, both virtual and physical. Scaling from 50Mbps in the branch office up to 240Gbps in the data center. Deployment as a dedicated appliance or as a service in an ASA 5500X series firewall. Already have a perimeter firewall solution but you’re still looking to add IPS, Application Visibility and Control? FirePOWER can deploy both as an inline appliance or passive detector behind an existing network appliance, tapping into existing network switching. For more information visit:
Cisco FirePOWER has many deployment options, both virtual and physical. Scaling from 50Mbps in the branch office up to 240Gbps in the data center. Deployment as a dedicated appliance or as a service in an ASA 5500X series firewall. Already have a perimeter firewall solution but you’re still looking to add IPS, Application Visibility and Control? FirePOWER can deploy both as an inline appliance or passive detector behind an existing network appliance, tapping into existing network switching. For more information visit:
http://www.cisco.com/c/en/us/products/security/asa-firepower-services/index.html
http://www.cisco.com/c/en/us/products/security/firesight-management-center/index.html
http://www.cisco.com/c/en/us/products/security/amp-appliances/index.html
http://www.cisco.com/c/en/us/products/security/fireamp-endpoints/index.html
- Justin Terry | Network Engineer