
| Photo by Samuel Corum/Anadolu Agency/Getty Images |


| Photo by Samuel Corum/Anadolu Agency/Getty Images |
Topics: Data Security, cybersecurity

Julian Assange and WikiLeaks have decided to publish an archive of 200,000 confidential Sony emails and documents leaked by a data breach at the end of 2014.
Last November, Sony Pictures Entertainment (SPE) suffered a massive data breach at the hands of a hacker group calling themselves "Guardians of Peace." U.S. intelligence officials suspected the group to be linked to the North Korean government, but North Korea denied responsibility.
Topics: Data Security

Laziness and convenience go hand in hand, but Amazon's latest creation has taken the former to extraordinary new heights. That in itself is an astonishing feat, considering how easy it is to order almost anything through a few mouse clicks - a sofa, TV, food, you name it.
Topics: New Technology
Severe data breaches suffered by Sony, Anthem and other companies over the last year further solidify the importance of data security.
Large companies continue to endure targeted attacks. Earlier this week, Twitch.tv publicly announced they had fallen victim to a data breach that possibly endangered users' personal account information.
So what makes this breach a big deal? If you haven't heard of Twitch before, here's what they're about: "Twitch is the largest live video platform and community for gamers with more than 100 million visitors per month. We want to connect gamers around the world by allowing them to broadcast, watch, and chat from everywhere they play."
A year ago, the Wall Street Journal published an article analyzing U.S. Internet traffic with data from DeepField.com. They found Twitch.tv to account for 1.8% of American peak traffic, ranking fourth overall and impressingly beating out companies such as Amazon and even Facebook. Only three titans saw more traffic than Twitch: Netflix, Google and Apple.
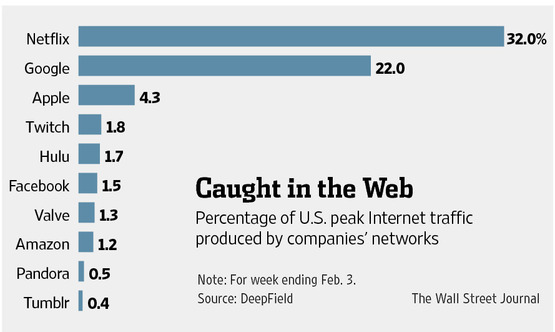
At the time, Twitch's Vice President of Marketing Matthew DiPietro said the site "is the central hub for the entire video game industry to share their passion for games."
And hackers have breached this massive hub. A hub that has undoubtedly grown even larger in the past year.
Fortunately, Twitch responded to the attack by providing disclosure to its users. It dispatched emails detailing the information that hackers may have obtained:
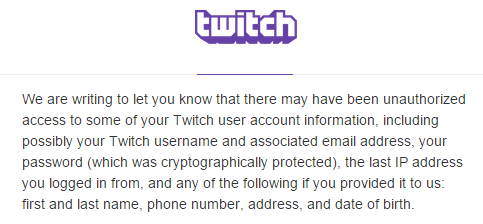
Well, at least credit card information isn't on there. Consolation prize acquired!
In addition to the email, Twitch took action. For the sake of protecting people's personal data, every Twitch account was forced to undergo a password reset henceforth. Not only would everyone have to make a new password, but that password would have to be actually strong, determined by their revamped algorithmic rating system. Otherwise, it would not be accepted.
Essentially, Twitch offered some basic, but eternally useful guidelines on enhancing password security. They used a range of ranked examples to illustrate their point.
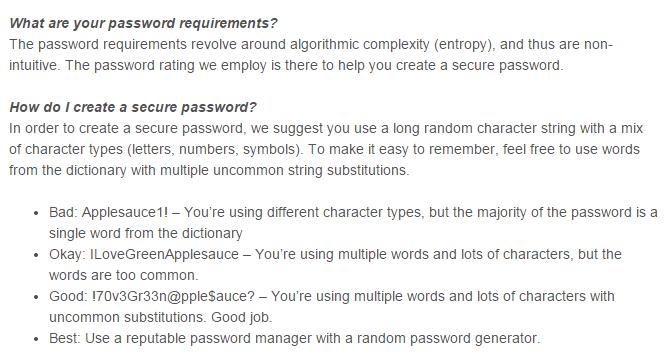
The more random a password is, the more effective it becomes. However, it's a little painful to use symbols and non-letters (!, @, $, etc.) in a password, isn't it? Passwords are something you often type out manually, and perhaps even from memory. Symbols don't quite lend to making that process convenient.
But as Twitch recommends, the most secure form of password security may lie within a password manager and random password generator, although they don't recommend any.
Effective password managers tend to be gated by a paywall. However, LastPass sports a beginner-friendly free version with enough features to help you feel safe, including two factor authentifcation and security alerts (but mobile access comes with a fee). KeePass is completely free and is even open source, but lacks some features and demands user customization to be truly effective.
Lifehacker produced a helpful chart that can help you determine which manager would suit you best:
Ultimately, the wisest course of action is to swiftly change your password to a site when it reveals it has been breached. Change your passwords used on other sites, too, if they are similar to the one from the compromised site. Password managers will help to facilitate this process.
Topics: Data Security

Spreading malware such as CryptoLocker is the cowardly, distant method for breaching a victim's data security and extorting money out of them. By comparison, social engineering is the method a bold-faced, audacious hacker will employ. It often involves the hacker directly tricking the victim via a manipulative phone call conversation.
Topics: Data Security