Disguised payment requests are the result of financial losses for companies whose employees have been targeted and spammed with fraudulent emails. These Company exec posers, got their recipients to process payments for non-existent goods or services. They did it with a fake wire and/or card transfers.
This is a great example of social engineering and the W-2 phishing scam that had happened earlier this year.
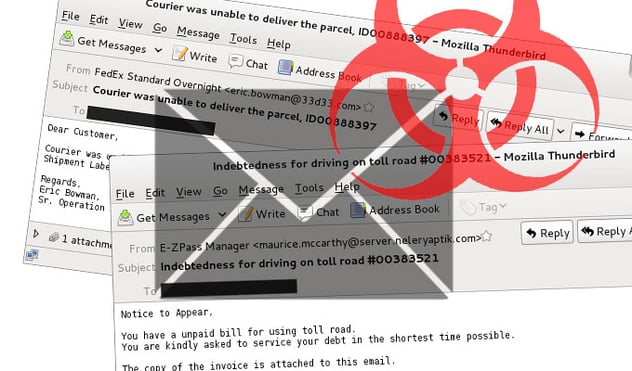
How is the email set up?
The scammer pretends to be the CEO or a senior executive of an organization. The scammer’s domain is very similar to the targeted domain. For instance, the poser sneakily adds or subtracts a letter from the domain name.
As an example the poser would register the domain as exaampleddomain.com. If an employee receives the email, the email would be CEO@exaampledomain.com. And now this new domain name with it's subtle difference, will cost a major financial loss to the unsuspecting company. The fake emails are usually sent to the finance department as they are only ones usually who are able to receive payment requests. The emails are usually sent out the same day the domain names are being produced.
How to prevent this from happening to your Business!
- Always check the sender’s domain name….CHECK CAREFULLY!
- If there any suspicion is triggered, make sure to let your IT department know immediately and any other department members who may be spammed along with upper management.
- The fake emails sometimes have file attachments such as PDF files that contain credit transfer instructions, DO NOT CLICK on these either, they could be malware.
Sources: https://www.symantec.com/connect/blogs/scammers-pose-company-execs-wire-transfer-spam-campaign
https://www.linkedin.com/pulse/scammers-pose-company-execs-wire-transfer-spam-campaign-furness
