Access: “The ability and means to communicate with or otherwise interact with a system, to use system resources to handle information, to gain knowledge of the information the system contains or to control system components and functions” (Nicc.us-cert.gov).
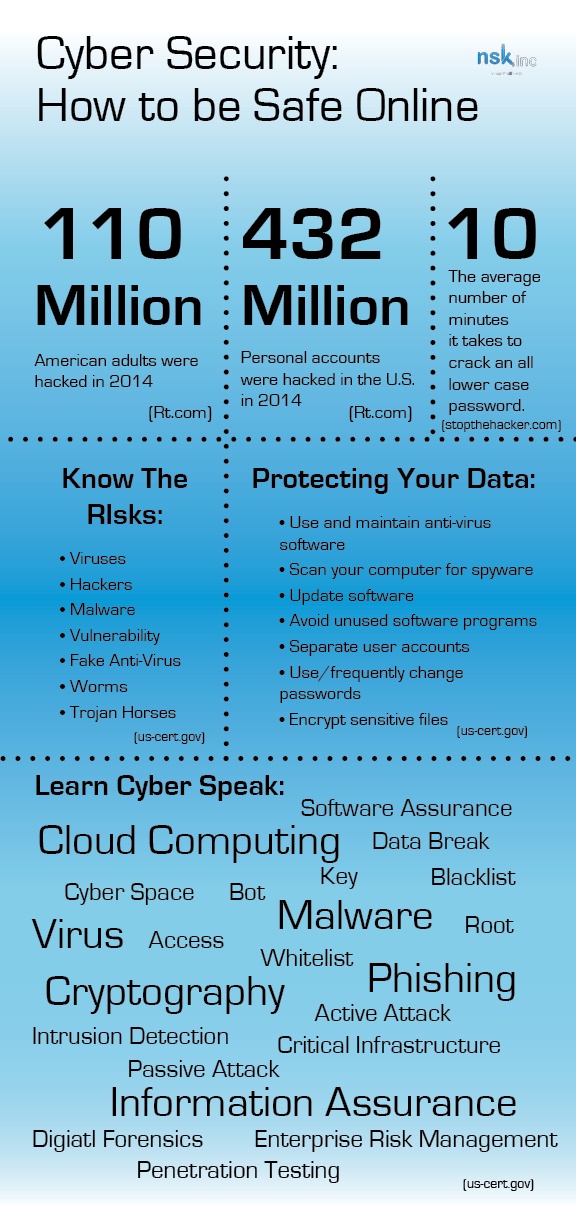
When you login on your computer, you have access to it and all the files, programs, and personal information stored on your account. An easy way to keep this information safe and secure is to use passwords. It is recommended that you change your password every 90 days, and you should always use a mixture of lowercase, uppercase, numbers, and symbols. On average, according to “stopthehacker.com,” it takes a hacker 10 minutes to crack an all-lowercase password that is 6 characters long. By adding other elements such as uppercase letters and numbers, that time jumps to an average of 3 years.
Another easy tip, which I mentioned in my previous blog post, is to practice the Principle of Least Privilege (POLP). By setting up separate accounts on your business or personal computer, you restrict access to information and prevent the use of unnecessary programs.
Active Attack: “An actual assault perpetrated by an intentional threat source that attempts to alter a system, its resources, its data or its operations” (Nicc.us-cert.gov).
Active attacks are what are most commonly thought of when the term “hacking" is used. Unlike passive attacks, which I will define a little later, an active attack would be something like a “denial of service” attack. The easiest way to avoid these types of attacks is by deleting potentially malicious spam mail, and not clicking on pop-up ads.
Blacklist: “A list of entities that are blocked or denied privileges or access” (Nicc.us-cert.gov).
In the simplest of terms, a blacklist is the set of programs, websites, accounts, etc. that have been blocked on your computer to prevent unintentional access. Google, Symantec, and Sucuri all have internal blacklists of sites that have been recorded to have malware. While you can still click the link and go to the site, these companies will show you a warning before allowing you to continue.

Bot: “A computer connected to the Internet that has been surreptitiously/secretly compromised with malicious logic to perform activities under the remote command and control of a remote administrator” (Nicc.us-cert.gov).
Bots are most commonly used on the Internet when a website, program, etc. intends on mimicking human behavior. For example, online chat sites commonly have bots to generate some repetitive conversation between a bot and an actual human user. Unfortunately, a bot's ability to emulate human interaction has made them a prime tool used by hackers to manipulate personal information. By programing a bot to perform a certain function, for example, have a simple conversation about where you live and who you are, a remote hacker can use that gathered information to access your information.
The biggest trouble with bots is how incredibly difficult it can be to distinguish between a bot and a human being. The best advice is to always try to be aware of who you’re talking to online and avoid suspicious sites.
Cloud Computing: “A model for enabling on-demand network access to a shared pool of configurable computing capabilities or resources (e.g., networks, servers, storage, applications and services) that can be rapidly provisioned and released with minimal management effort or service provider interaction,” (Nicc.us-cert.gov).
Cloud computing is one of the most popular forms of data storage and interaction on the market today. Rather than relying on a personal computer or local server, putting your information online makes it easy for not only you to access it anywhere, but also for your employees to access it anywhere. The danger with this is that hackers can also find ways to access this shared information.
By using a reliable back up/disaster recovery program, you can ensure that even if a hacker somehow gets your information and attempts to change it, your actual information will remain secure. NSK Inc. offers its own solution for this problem and then some. Pavis Back Up and Disaster Recovery is a program that NSK provides that gives you the scalability of a public cloud, ensuring you have plenty of space for all your work, but also the privacy and security of a private cloud. Using a program like this is the best way to keep your data secure.

Critical Infrastructure: “The systems and assets, whether physical or virtual, so vital to society that the incapacity or destruction of such may have a debilitating impact on the security, economy, public health or safety, environment or any combination of these matters” (Nicc.us-cert.gov)
In the United States alone there are 16 critical infrastructure sectors. While critical infrastructures can vary in size, from international to even a family household, they are no less important. It requires a combination of all these security tips together to ensure that this aspect of your computer, business, etc. stays safe.
Cryptology: “The use of mathematical techniques to provide security services, such as confidentiality, data integrity, entity authentication, and data origin authentication” (Nicc.us-cert.gov).
In layman's terms, cryptology is the study of codes and the art of writing and solving them.
Cyberspace: “The interdependent network of information technology infrastructures, that includes the Internet, telecommunications networks, computer systems and embedded processors and controllers,” (Nicc.us-cert.gov).
Data Breach: “The unauthorized movement or disclosure of sensitive information to a party, usually outside the organization, that is not authorized to have or see the information” (Nicc.us-cert.gov).
Digital Forensics: “The process and specialized techniques for gathering, retaining and analyzing system-related data (digital evidence) for investigative purposes” (Nicc.us-cert.gov).
Originating in the personal computing revolution of the 1970s, digital forensics didn’t truly take form as we know it today until the early 2000s. Expanding from personal computers to all forms of storage devices, digital forensics is the method that IT professionals and even government agencies use to investigate crimes, often computer related crimes. By searching through whatever stored data is left on a device, professionals can attribute actions to an individual based on meta data, confirm or rebut alibis, search web history to find intent, authenticate a document, and even evaluate a source to see if it originated from a specific device.
Enterprise Risk Management: “A comprehensive approach to risk management that engages people, processes, and systems across an organization to improve the quality of decision making for managing risks that may hinder an organization’s ability to achieve its objectives” (Nicc.us-cert.gov).
Information Assurance: “The measures that protect and defend information and information systems by ensuring their availability, integrity, and confidentiality” (Nicc.us-cert.gov).
Intrusion Detection: “The process and methods for analyzing information from networks and information systems to determine if a security breach or security violation has occurred” (Nicc.us-cert.gov).
Key: “The numerical value used to control cryptographic operations, such as decryption, encryption, signature generation or signature verification” (Nicc.us-cert.gov).
Relating back to cryptology, a key is the password that solves a code.
 Malware: “Software that compromises the operation of a system by performing an unauthorized function or process” (Nicc.us-cert.gov).
Malware: “Software that compromises the operation of a system by performing an unauthorized function or process” (Nicc.us-cert.gov).
Malware is one of the most common risks for any Internet user. It is kind of the umbrella word to include the majority of the awful things that people have designed to corrupt and change data on other people’s computers. While there are enough examples of malware to fill a novel, there are some basic types that are easily described. The general categories are: Adware, spyware, bots (which we’ve already covered), bugs, ransomware, rootkits, Trojan horses, viruses, and worms.
Passive Attack: “An actual assault perpetrated by an intentional threat source that attempts to learn more or make use of information from a system but does not attempt to alter the system, its resources, its data or its operations” (Nicc.us-cert.gov).
While an active attack means that a hacker is purposefully changing data in order to get the information they want, a passive attack means that the hacker is simply watching. While that seems far less severe than someone trying to actively break into your system, by analyzing a user’s behavior on their machine, a hacker can do just as much damage with half the chance of being caught.
Penetration Testing: “An evaluation methodology whereby assessors search for vulnerabilities and attempt to circumvent the security features of a network and/or information system” (Nicc.us-cert.gov).
This is basically a way for IT professionals to test and see if your operation system, software, etc. has any vulnerabilities. By placing a simulated malicious attack into the system, the entire network is checked for weaknesses that can then be amended.
Phishing: “A digital form of social engineering to deceive individuals into providing sensitive information” (Nicc.us-cert.gov).
Root: “A set of software tools with administrator-level access privileges installed on an information system and designed to hide the presence of the tools, maintain the access privileges and conceal the activities conducted by the tools” (Umuc.edu).
Software Assurance: “The level of confidence that software is free from vulnerabilities, either intentionally designed into the software or accidentally inserted at any time during its lifecycle, and that the software functions in the intended manner” (Nicc.us-cert.gov).
Virus: “A computer program that can replicate itself, infect a computer without permission or knowledge of the user, and then spread or propagate to another compute,” (Nicc.us-cert.gov)
Whitelist: “A list of entities that are considered trustworthy and are granted access or privileges” (Nicc.us-cert.gov).