What is a NextGen Firewall

A “NextGen” Firewall, is a firewall that does all of the traditional stateful inspection of traffic, but also includes deeper inspection of the payload. This can include features like Anti-malware/Spyware, URL Filtering, Traffic Decryption, Intrusion Detection, Intrusion Prevention, and Geo-blocking.

Why use a NextGen Firewall
NextGen firewalls are incredibly useful in gaining visibility into the traffic coming in and going out of the network. This information is particularly valuable when trying to assess the impact of a security breach or detection of one before it impacts users. In previous years, you’d have to utilize 4-8 different appliances to accomplish the same tasks that one, or one pair of NextGen Firewalls can do. The other benefit to this is that all these systems and software can be aware of each other. This means that event correlation is easier within that type of a platform.
How is this different from what I do today?
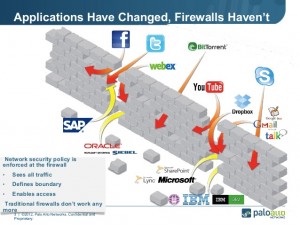
Just because you have a firewall doesn’t mean that you are doing a great job at managing your security. These nextgen firewalls are the next evolution of security in the network. The applications that we use have changed significantly. At a basic level, we have done much of our security based on the OSI model’s Layers 3 and 4. Layer 3 and 4 bases security on IP address and TCP/UDP ports. As an example, if we are protecting a mail server we block access to the mail server on all ports except TCP 25 (SMTP). This was good enough when mail first started, as it solved most of our security needs. Now most applications happen over HTTPS (TCP Port 443) because many of our applications are SaaS or Web based. Even if you use the mail example a lot of us are using Outlook Web access, gmail, or Office 365. All of these services occur over TCP port 443 (HTTPS). This means we can no longer categorize the type of traffic just based on the TCP or UDP port it traverses. Enter the NextGen Firewall, which now can dig deeper into the payload of the transmission. This allows for behavioral inspection of the traffic, meaning that instead of just blocking or allowing the traffic based on TCP or UDP port, they actually look at where/how the traffic is behaving. They can apply some intelligence and block or allow based on a variety of signature that identify malicious traffic.
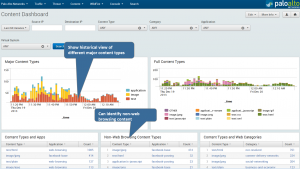
Reporting is significantly better!
Something great about this new style of inspection and detection has driven manufacturers to create strong reporting capability. Below is an example of a Palo Alto dashboard that is part of their Splunk App. Splunk is a great way to keep this data for an extended period of time and do long term analysis on it.
What to do next?
If you think this is something you would like to pursue contact your Focus account manager and talk to them about Palo Alto, Cisco Firepower, and Splunk. If you like it we can assist with acquisition of the licensing and design a final solution.
Thanks for reading!
Brad Maher | Director of Technology