VMware NSX Security
VMware has been working on enhancing the security in the Virtual Datacenter for a while now. NSX is a few years into it’s production lifecycle. We’ve seen several major revisions as well as a 3rd party partner eco system develop. NSX is really divided up into two parts, Security and Routing/Network services. In this post I’m going to cover the NSX security components. That’s not to discredit the Routing and Network service components, because there is great value in those, however they have their place and there is a lot of features related to it. The routing part really needs it’s own post. Nonetheless the two components are included in the product when you license it.
production lifecycle. We’ve seen several major revisions as well as a 3rd party partner eco system develop. NSX is really divided up into two parts, Security and Routing/Network services. In this post I’m going to cover the NSX security components. That’s not to discredit the Routing and Network service components, because there is great value in those, however they have their place and there is a lot of features related to it. The routing part really needs it’s own post. Nonetheless the two components are included in the product when you license it.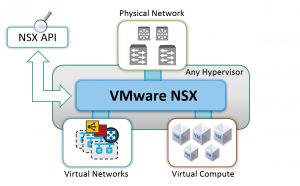
The above diagram is a good start to explaining NSX. It is integrated into the hypervisor, so it is able to interact at the kernel level and enables the 3rd party ecosystem to access information it never had access to in the past. Historically if you wanted to enforce any type of security between VM’s, you had to route traffic through an external firewall/security device. This requires the use of very highend hardware platforms to be able to support the inspection of traffic at LAN speed. NSX will give us this visibiltiy along with our favorite security partner integration. There is however one major name missing from the list on the 3rd party partner integration. Cisco, is choosing not to participate at this time and I’m going to take a short paragraph to discuss this.
Cisco belives they have a better solution. I think that’s great, because Cisco is correct most of the time. In fact Cisco helped VMware design the original virtual networking components in ESX. You can still see a reminent of that collaboration, VMware supports CDP (Cisco Discovery Protocol) in the standard vSwitches, they also support Private VLAN’s on distributed vSwitches. All of that said, we are a Cisco partner too, and it appears that ACI is Cisco’s answer to NSX. ACI has some great attributes to it, and at some point we’ll do a blog post on it too. From what I’ve seen so far it does require specific hardware, and in some cases will require a forklift upgrade to enable across your datacenter. For this reason I think a lot of our customers will shy away from it, but it’s too early to tell, so I’ll leave it at that and continue on with NSX.
As of December 2015, VMware has fewer than 1000 production implementations of NSX, so it’s still early in the process. However, some of the largest organizations in the world are represented in the 900+ production installations out there. Like most other cutting edge security technologies it seems the large enterprises are adopting first mostly out of need. We’ve seen huge security breaches with large enterpises such as Home Depot and Target, involving payment processing information, none the less, these large enterprises have the most to gain from these new technologies. I believe this has helped develop the 3rd party partner integration. The third party ecosystem is critical to the success of security in your datacenter. Without companies like Palo Alto, Trend Micro, Splunk, etc. you can’t integrate your existing toolset into the datacenter security.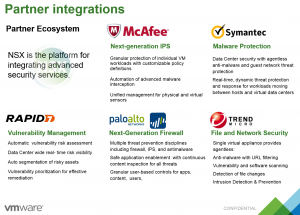
How does it work?
NSX has some unique capabilities. First off we need to talk about segmentation of traffic. In some cases we don’t want VM’s talking to each other at all. This would be called isolation. In other cases we only need them to communicate on certain ports or with certain services. This is referred to as segmentation. Lastly, we need to bolt on our advanced services like IPS/IDS, malware protection, URL filtering, etc. These services come from 3rd party typically. All of this can be done with NSX, while the last part usually requires some 3rd party help.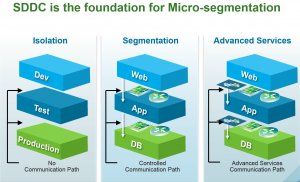
NSX can accomplish this by inspecting and enforcing rule set at the VMnic level. This means my policy can be unique on an individual VM basis. Not only that, but I can also enforce policy between VM’s on the same network segment!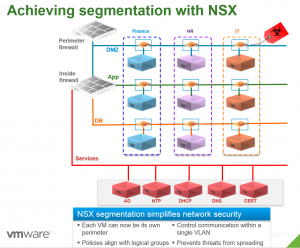
What to do next?
If you think this is something you would like to pursue contact your Focus account manager and talk to them about NSX. We can setup and meeting and discuss what business problem NSX can solve for you. If you like it we can assist with acquisition of the licensing and design a final solution.
Thanks for reading!
Brad Maher | Director of Technology
