Anyone who’s been following the security pundits and keeping an eye on the threat landscape can tell you that 2016 is being hailed as the year of ransomware. Sensationalist click-bait headlines aside, experts agree that ransomware is more than just the latest vulnerability that happened to make the headlines, and any business that relies on computers (are there any left that don’t?) can’t afford to ignore this. If you must TLDR, at least skim the minimum info below.
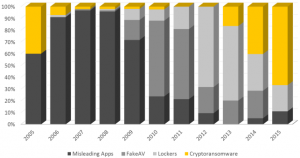 CryptoRansomware has already become the malware of choice by end of 2015. Source: Percentage of new families of misleading apps, fake AV, locker ransomware and crypto ransomware identified between 2005 and 2015 – Symantec
CryptoRansomware has already become the malware of choice by end of 2015. Source: Percentage of new families of misleading apps, fake AV, locker ransomware and crypto ransomware identified between 2005 and 2015 – Symantec
“There are two types of organizations now: those who have been breached and those who have been breached but [don’t] know it yet. 2016 will be the year of…ransomware” – James Scott, Sr Fellow Instititute of Critical Infrastructure Technology
Don’t believe me? Maybe this will hook you to keep reading. According to a report from the Cyber Threat Alliance, US companies suffered $325M dollars in damages in 2015[i]. There’s no shortage of whitepapers, blogs, and articles to load up on your Pocket app for the subway or your next flight, so my intent is to boil down to the most urgent facts, as succinctly as possible to give you the leverage you need to motivate the decision makers above you, and maybe help you recover faster when you get hit.
The minimum info:
While I don’t fully agree with James Scotts dire quote above, I do believe that anyone who hasn’t been breached yet will - it’s a nigh-mathematical-certainty. There’s simply too many attack vectors, too much potential for human error, too little user training, and too many highly motivated bad actors.
- Backups are your best protection – including a good retention policy in case your backups get encrypted too
- Antivirus, spam protection, and legacy firewalls do not guarantee protection – I’ve personally worked with four victim companies, all of which were using all of the above, from respected brands
- Paying the ransom doesn’t guarantee you get your data back, and many recommend against it
- Any company can be hit – this is not limited to large, high profile companies – those are just the ones that make the news
- No budget for user training? Average cost for security training per end user per year - $30 vs. Identity Protection per customer per year after a breach - $300
- The attack vectors are myriad and new ones are being discovered routinely, but include Word and Acrobat macros, malvertisements on websites (even highly reputable sites, like the Wall Street Journal
- Ransomware is on pace to be a $1 Billion industry – FBI, reported by CNN Money[ii]
Some definitions:
- Ransomware: Malicious software that restricts access to the infected system, requiring the user to make a payment to the malware operators, frequently by encrypting important files
- Cryptolocker: A variant of ransomware, it’s become somewhat synonymous with any ransomware that encrypts your files, as it was one of the first to make headlines
- AES Encryption: government grade encryption, considered sufficient to thwart any reasonable attempts to break due to computational complexity
- C&C - Command and Control: one or more systems on the internet capable of issuing commands and harvesting data from a compromised computer
- I2P - Invisible Internet Project: known as a ‘darknet’ or overlay network, allows communication between systems across the internet with greater anonymity and less opportunity for 3rd party tracking
“There’s no one method or tool that will completely protect you or your organization from a ransomware attack, but contingency and remediation planning is crucial to business recovery and continuity—and these plans should be tested regularly.”
– James Trainor, FBI Cyber Division Assistant Director[iii]
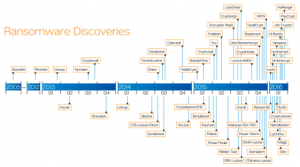
The variants:
Believed to have been first detected on the internet as early as September of 2013, Cryptolocker was one of the first high profile ransomware viruses, garnering its progenitors an estimated $3 million US dollars before authorities were able to shut down the group responsible. Meanwhile Cryptowall springs up, and brings in $18 million. Since then, Trend Micro reports a list of at least 49 different families of Ransomware. Some major players are highlighted below:
- CryptoWall 3.0: uses AES encryption on your files, and then the key is also AES encrypted with a unique public key – effectively uncrack-able. Communicates with C&C via I2P network proxies, currently most prolific ransomware
- TorrentLocker: uses spear phishing, posing as utilities service, targets individuals and businesses
- CTB-Locker: Curve-Tor-Bitcoin, uses ECC encryption, disseminated via spam mail in high volume
- TeslaCrypt: upgraded version of CryptoLocker, second most prolific worldwide, usually phishing or spam emails
The point here is, the bad guys are working with tremendous intensity on improving their craft – possibly more so than we’ve ever seen in the past. There’s real, serious cash to be made, and they’re going after it, in an organized fashion. You can even pay for ransomware as a service now! As part of your package, you’ll get access to one of the latest ransomware viruses, with a helpful FAQ on how to configure where you would like your ransom sent and in what denomination (Bitcoin is hot right now). But, you’re a busy hacker, you don’t have time to sit on the phone with your victims to accept financial transactions – have no fear, there’s a staffed, 24x7 call center included in your package! You can’t make this stuff up.
“Never before in the history of human kind have people across the world been subjected to extortion on a massive scale as they are today.” - Symantec[1]
From the trenches:
As previously mentioned, I’ve had the (mis)fortune to work with several customers whose businesses were impacted by Cryptolocker or Cryptowall. Here’s what we observed and learned from our first battle with Cryptolocker.
This customer is using a well-known web filter to prevent browsing to questionable sites. They also employ a very solid firewall and modern AV, and we patch their servers monthly – a model IT infrastructure. Their environment is based almost entirely on VMware Horizon View – expected by many to be more resilient to virus infections, in that you can just refresh a desktop that’s been impacted (and this is frequently true).
Users reported trouble accessing files one morning. Cursory investigation showed that many files throughout many directories were encrypted and inaccessible. First point: users detected this – the firewall, the web filter, and the client and host-level AV did not make a peep. Second point: thanks to reasonably secure folder permissions, not all data was encrypted, so some departments were able to continue functioning. If any of your employees have domain admin access across all file shares, this should give you pause - the average time from infection to file encryption is 3 minutes.
Once we identified the user, (the encrypted files were modified by that user’s username) the VDI desktop was refreshed to eliminate the virus.
Luckily, we host their backups in our private Avamar cloud, so we were able to restore tens of gigs of data very quickly, with minimal effort. The next day, we get reports of newly encrypted files. Third point: the virus later turned out to have its hooks in the user profile, so refreshing the desktop did not eliminate it. We engaged with the AV vendor to nail down the virus, who determined it was a variant they’d not seen before (aka Zero-Day)but were able to provide an early release definition patch, so after a final AV scan and then one more pass restoring the odd file here and there, the issue was resolved. Fourth point: AV is not infallible, even when fully updated, because zero-day variants don’t match any definitions, and heuristic scanning can only do so much.
Post Mortem: The user attempted to bypass the proxy settings that routed his web traffic through the filters. Fifth point: user training may have prevented this behavior. Because the user was in the wrong OU, the wrong security policy applied, next thing you know the user contracts a Cryptolocker variant from a drive-by malvertisement from a sketchy website. Sixth Point: Human error during the user provisioning is ultimately what allowed this to transpire. The users files, and all files he had access to on the network, were encrypted in short order. No monitoring tools, no firewalls, no AV detected this, until a user reported problems accessing those files the next morning.
So now what?
Backups! There’s nothing better than backups. You can’t break the encryption, you can’t stop every spam message, every Word macro, every Flash vulnerability, every Java memory leak exploit, and every non-techie executive that wants to see what that attachment holds. All you can do is plan on how to deal with the situation when it happens, and that will include a solid backup plan. Keep in mind, if you don’t detect that your files are encrypted before your nightly backup run, that nights backup will be a copy of your files encrypted and will be useless to you. Retention periods are critical here – you may need to go back a day or two – or even several. It’s expected that variants of ransomware will be specifically engineered to look for and encrypt backups, and/or to hide until some time has passed before declaring their ransom demands, in the hopes that your backups are irreversibly encrypted too.
Security in-depth – it’s a term many throw around, but not everyone lives it. Naturally you have to balance security with the efficacy of your employees – it’s a balancing act.
Cisco’s FirePower product is impressively powerful, and the only product I’ve used to date that would’ve made a dramatic difference in each infection scenario I’ve worked on. It’s aptly named - if you want weapons-grade protection, look into this. Want end to end visibility of communication from outside sources to your internal hosts? Want to know what protocol they were using? Want to get retroactive notifications if a file previously allowed through has since been identified as potentially dangerous? Want your firewall to automatically start blocking traffic based on suspicous behavior - based on rules you configure? You got it!
Firewall – keeping up to date with modern hardware (and software/os updates) may not stop that much in the way of viruses, but can limit command and control interaction post-infection.
Web content filtering – Protecting users from themselves is worth the effort – a study by Verizon indicates that 35% of security attacks originated from web sites or applications.[iv] Every single virus infection I’ve dealt with in 17 years has originated from either a website, or an email attachment.
Mail filtering – This one is particularly critical. Every single virus infection I’ve dealt with in 17 years has originated from either a website, or an email attachment – with home users, it’s typically websites, and corporate users it’s almost invariably an email attachment.
User Permissions – Limit users to what they need access to, and eliminate domain admins from everyday use. Instead, give your sys admins secondary accounts, so they can elevate certain processes as needed – it sounds much more painful than it really is, I’ve been there, you get used to it.
Backups – Did I mention backups? Do you know for a fact you can restore to last night? How about the night before? Or last Friday? Seriously, stop reading this and go check. You’ll thank me later.
[i] http://cyberthreatalliance.org/cryptowall-infographic-stats-full.pdf
[ii] http://money.cnn.com/2016/04/15/technology/ransomware-cyber-security/index.html?section=money_technology
[iii] https://www.fbi.gov/news/stories/2016/april/incidents-of-ransomware-on-the-rise/incidents-of-ransomware-on-the-rise
[iv] http://6scan.com/ebay-security-and-the-punching-bag-of-the-internet/
