SDN accomplishes these business objectives by converging the management of network and application services into centralized, extensible orchestration platforms that can automate the provisioning and configuration of the entire infrastructure. Common centralized IT policies bring together disparate IT groups and workflows. The result is a modern infrastructure that can deliver new applications and services in minutes, rather than days or weeks required in the past.
SDN delivers speed and agility when deploying new applications and business services. Flexibility, policy, and programmability are the hallmarks of Cisco's SDN solutions, with a platform capable of handling the most demanding networking need of today and tomorrow.”[1]
2. Supranet – “The Supranet is the network communication infrastructure that represents the symbiotic relationship between the electronic and the physical worlds. The crux of the Supranet concept is the connectivity of embedded computers, wireless networking, bidirectional interfacing technology, and applications that are adaptive across various devices. Mobile business, or m-business, is considered the primary driving force behind the continued development of the Supranet.
 This term was first coined in 2000 by the US-based information technology research and advisory firm Gartner, Inc. as part of its framework analysis on convergent communications. The concept was further developed as part of a series of seminal research papers published by Gartner employees over the course of 2001. Over the years, the term never became quite as ubiquitous as the word “Internet,” but some of the definitions and subsumed terms that fleshed out the concept have become popular, and many of the underlying concepts and predictions have proven prescient.
This term was first coined in 2000 by the US-based information technology research and advisory firm Gartner, Inc. as part of its framework analysis on convergent communications. The concept was further developed as part of a series of seminal research papers published by Gartner employees over the course of 2001. Over the years, the term never became quite as ubiquitous as the word “Internet,” but some of the definitions and subsumed terms that fleshed out the concept have become popular, and many of the underlying concepts and predictions have proven prescient.
The physical word, or p-world, that is part of the Supranet definition is comprised of the tangible objects such as paper, houses, people, and vehicles that need to be connected to the electronic world, or e-world, of devices, such as phones, computers, cameras, and televisions. Under the Supranet concept, the e-world devices are connected to the p-world through embedded computers with bi-directional interfacing that allows the device to transmit identifying information about the user or uniquely tag the information being transmitted. Wireless networking and smart application architecture that can adapt across devices and allow profile management is what powers the information exchange between worlds.
Gartner theorized that the development of mobile business would drive the development of the Supranet. Mobile technologies, such as Bluetooth, GPS, geotagging, and Wireless Application Protocol, that make communication between the physical and electronic worlds easier and more secure support the mobile Supranet lifestyle. People using the Supranet can be connected anytime and anyplace, and can be located and tracked through the devices they use, ultimately benefiting electronic commerce.
A natural progression of the Supranet is the increasing convergence of the physical and electronic worlds into a virtual world that mirrors the real world with increasing precision. Products, such as gaming systems, that convert three-dimensional movement in the real world to movements in a digital landscape are an example of the Supranet at work. Many of the location-mapping and geo-tagging products offered other Internet companies are also examples of the Supranet concept in practice.”[2]

3. The Internet of Things/Internet of Everything - (IoE) “In one sense the IoE presents a familiar, idyllic image of the future, the image of the “smart” house responding to every person’s move automatically and precisely, the truly universal remote (an iPhone, perhaps), controlling whatever isn’t automatically done. For Example: Apple’s innovations are getting devices talking better than ever. Indeed, supporters of IoE agree technology should be talking about everything, if it can. Detractors believe it should not, that some things are sacred anti-data ground. Human value, for example, put in terms of data is reductive, ignores the importance of human interaction in a human world.”[3]
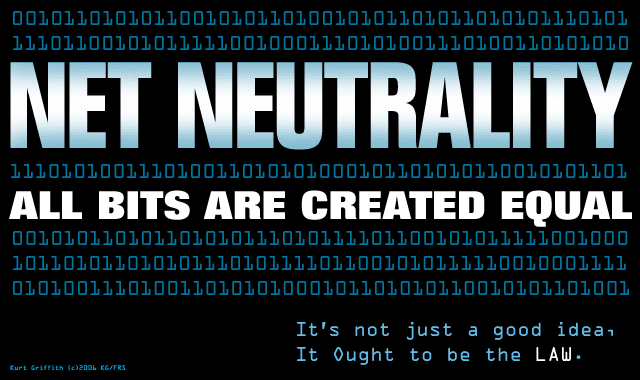
4. Net Neutrality -It is, simply, the concept that all Internet traffic should be treated equally, that no one entity, however large or small, should have more or less access to data transfer than another. This is so intrinsic to the way we expect the Internet to work that it’s difficult to imagine the opposite, an Internet in which data transfer speed – Internet speed – is bought into instead of de facto had.[4]

5. Node – A node is any system or device that is connected to a network. For example, if a network connects 1 file server, 10 computers and 4 printers, there are 15 nodes on the network. Every node has a unique network address, sometimes called a data link control (DLC address or Media Access Control (MAC) address
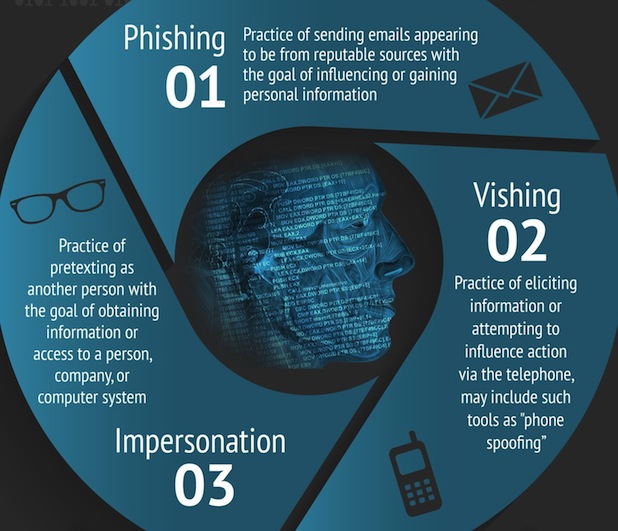
6. Social Engineering – Social engineering is the art of manipulating people so they give up confidential information. The types of information these criminals are seeking can vary, but when individuals are targeted the criminals are usually trying to trick you into giving them your passwords or bank information, or accessing your computer to secretly install malicious software–that will give them access to your passwords and bank information as well as giving them control over your computer.
7. Phishing – The act of sending an email to a user falsely claiming to be an  established legitimate enterprise in an attempt to scam the user into surrendering private information that will be used for identity theft. A Phishing email will direct the user to visit a website where they are asked to update personal information, such as a password, credit card, social security or bank account numbers, that the legitimate organization already has. The website however, is bogus and set up only to steal the information the user enters on the page.
established legitimate enterprise in an attempt to scam the user into surrendering private information that will be used for identity theft. A Phishing email will direct the user to visit a website where they are asked to update personal information, such as a password, credit card, social security or bank account numbers, that the legitimate organization already has. The website however, is bogus and set up only to steal the information the user enters on the page.
[1] CISCO
[2] WiseGeek
[3] blog.nskinc.com
[4] blog.nskinc.com
http://www.social-engineer.com/blog/