The world of cyber security is constantly changing. New viruses, malware, bots, and phishing scams are being developed every day to steal both business and individual user information. To counter this online battle, new security products are also being developed, all promising to be the best on the market and the best for you and your business. With all these options to sift through, the seemingly endless streams of data supporting this device and that supporting system, how do you choose this right one? Who has the time to sort through the products and companies while also having their own lives and business to deal with? Thankfully, there is a source available to everyone that’s entirely free to use that does that leg work for you.

Known as “Security Wizardry,” this information security portal provides the everyday user with well-organized folders detailing security product reviews and ratings. Not only this, but the website is also the portal “to the famous Talisker Radar Page.” The radar page is designed to update every 20 minutes, by a team of US and UK personnel, to provide practically live information as it develops about cyber security. The problem with the page is that upon your first glance, it is very obvious that the page was designed to suit the needs of the military and government. While normally I would say that feeling like James Bond is something to be proud of, in this instance, many users may feel more like Austin Powers with how much is going on, on the page. This post is dedicated to helping the everyday user earn their 007 status by breaking down the radar page for you into easy to digest sections.
Alert Details: Top Left
The Alert Details stream is a scrolling list of information, briefly detailing the most recent cyber security alerts happening every day. When you scroll over the list it will pause,  allowing you to read each segment at your own pace. If you click on the section, it will bring you to an expanded page in which you can read the full expanse of each alert and get a real understanding of the current threat level. This section is directly linked to the Computer Network Defence Alert State graphics that are shown in the middle of the page on either side of the site’s logo.
allowing you to read each segment at your own pace. If you click on the section, it will bring you to an expanded page in which you can read the full expanse of each alert and get a real understanding of the current threat level. This section is directly linked to the Computer Network Defence Alert State graphics that are shown in the middle of the page on either side of the site’s logo.
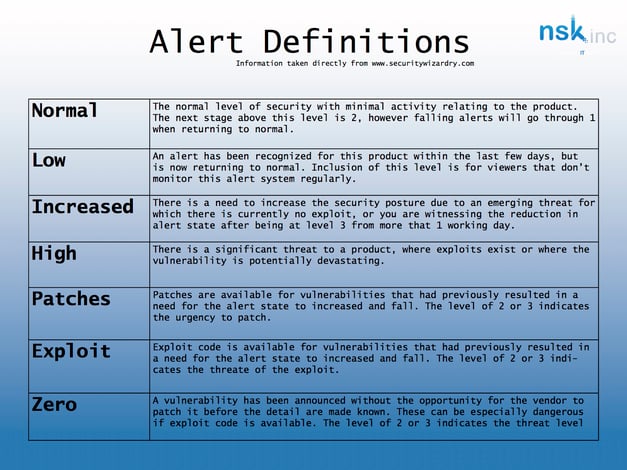
Computer Network Defence Alert State: Top Center
The small nblue charts in the middle of the page can be read much like the chart of a stock rating. Contrary to a stock rating however, a downward facing arrow and lower number is far more beneficial than an upwards arrow with a higher number. This graph is basically a simplification of the Alter Details list on the left side of the page with an added element. The color, number, and arrow are an indication for how serious the potential alert is and how long it is has been a problem. The definitions of each alert are as follows:
Security News: Middle Left
The Security News stream is located directly under the Alert Details section of the page. It scrolls through all the latest security related tech articles published on Securitynewswire.com. Much like the Alert Details stream, as you scroll over this section the scrolling will pause, allowing you to read each headline at your own pace. Clicking on any of these links will bring you to Security News Wire’s website where you can read the whole article and find other interesting and related pieces to read.
Internet Storm Center: Middle Center
The ISC is a basic graph designed to show the potential for “change” in malicious traffic throughout the day. Every computer that is connected to the internet is susceptible the malicious activity and the ISC is designed to show the risk of you, as a host, experiencing disruptions caused by malware online. If you click on the graph, it will bring you to the ISC's website where you can see an explanation of what the variations of their graph mean.
Team Cymru Malicious Activity Map: Bottom Center
The largest, and definitely most eye catching image on the page is the Cymru map of the world. This map is updated every day to show where malicious activity is happening around the world. Reading much like a heat map, the darker the color (blue and purple for example) the less malicious activity and the brighter the color (orange and red for example) the more malicious activity. However, the one problem with this graph is that hacking can occur far away from where the attack actually happens, so I would personally consider it a great estimation with the potential flaw of compromised information. If you click on the map and follow it to Team CYMRU’s page, you can download a movie version of the map to your computer that shows how the intensity fluctuated for that day’s data.

Virus News: Top Right
Virus news has the exact same design as the Alert Detail and Security News sections of the page. The scrolling design lists any and all new viruses or updates to old viruses that are relevant threats every day. Clicking on one of these links will redirect you to Sophos.com where you will see a chart detailing what category of malware it falls under, what type it is, the prevalence, when protection from this virus started being available, and the last time the information about that virus was updated. There are also links to get more information about that virus, the aliases of that virus, the operating systems that the virus is affecting, and recovery instructions. While it is always recommended that you contact your IT professional when you have any kind of computer problem, having a basic understanding of what your computer is dealing with definitely helps and also gives you the knowledge to prevent future problems.
Latest Tool Versions & Latest IDS Signatures: Bottom Right
This section is exactly what it sounds like. The page displays two small graphs in which names, dates, and version numbers are all listed in the simplest way possible. If you look at the right hand column where the version numbers are, that column is where you would click to be lead to each company’s website for further information. For example if Cisco IPS has released a new IDS signature, I would click on the link to the right of their name and I would be able to read all about when the signature was posted and what that means for me as a user of their products or a curious cyber security afishionado.
Useful Links: Bottom Right
This section is probably the most self-explanatory section presented on the page. The website defines the links as ones that their “analysts and radar patrons find useful.” These links range from the ISC’s website where they explain the meaning and correct use of their product, government websites that explain computer safety and regulations, and other sites that monitor the intensity of malicious activity around the world. It is in this section too that as a user, you find out that the website is welcome to any and all comments and suggestions for more useful links and website functionality.
Now that you know the layout of the website, get out there and make sure you’re being as secure as possible on the web!
