With protection and security at stake, as well as accountability, companies are looking to MDM, which makes business run as smooth as a knife slicing into butter.
In our previous post we discussed how businesses are favoring BYOD, and how this policy makes MDM an office-must. In this entry, we’ll cover MDM advantages and implementation.
Why MDM is Essential
A main perk about MDM is security.
BYOD is a plus for businesses because they save money on products by relying on employees working on their own devices. But can this reliance be volatile? Yes, and unintentionally so.
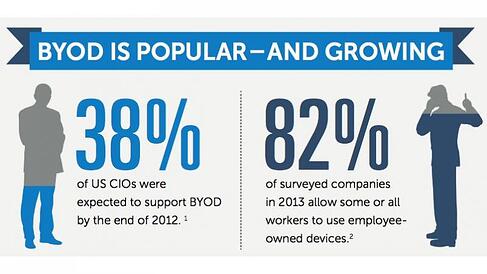
Think about it:
- Your smartphone is ranked up there with most-lost objects. (Are still looking for your car keys/TV clicker/Chapstick?)
- You are carrying your office wherever you go, on the same device you may let your kids play Bejeweled, pay bills, order from Amazon, and Instagram. Add that to your work’s login and data, and it’s amazing we’re not all super-gluing our phones to our palms.
- Accidents happen. You could “launder” your mobile device, forgetting it was in your left pocket. You could drop it. It could self-destruct. (…We’re sure the last bit is the least likely to happen.)
 So how can the above be resolved? We can’t guarantee you’ll remember to remove your phone from your coat pocket before it goes to the cleaner’s, but MDM and Managed IT Services can give you a sound mind when your smartphone is a tool you use for all matters of life besides your work.
So how can the above be resolved? We can’t guarantee you’ll remember to remove your phone from your coat pocket before it goes to the cleaner’s, but MDM and Managed IT Services can give you a sound mind when your smartphone is a tool you use for all matters of life besides your work.
Why an MDM strategy is beneficial for businesses
- Passwords and lost data can be recovered.
- You won’t have to stress over personal and company information getting in the wrong hands if you physically lose your device. Confidential information can be instantly erased.
- When a new employee hops onboard or a staff member chooses to upgrade and switch to a newer model for email/phone calls/Wikipedia searches/MenuPages orders, they can ease into the system without a hassle. Password setup and encryption can be set up quickly and easily.
- Centralized policy management means security over multiple platforms. Updates are automatic and systems are monitored.
Planning an MDM Strategy for Your Workplace
Implementing MDM is simple once you layout policies that will fit with how your company functions and guarantee company security. Here are some tips from Todd R. Weiss at computerworld.com
- Decide what devices will be used.
- Make sure these devices can handle the levelsof security required.
- Create device use policies that are clear and easy to understand so they’ll be effective. Be prepared to educate employees on company’s MDM approach.
- Make passwords mandatory.
- Consider legality issues.
- Because technology continues evolved, be aware that these policies will constantly change over time.
And so, considering all these advantages, having your company adapt MDM will create a secure and efficient working environment.
On one more note, we’ll leave you to guess what you can also “Bring Your Own” for good office morale…
Source: computerworld.com
Images: readwrite.com, gsmnation.com, bizexpocenter.com


