The following is an excerpted from an important blog by AppRiver on a new and highly dangerous Malware campaign
This morning we began seeing yet another new version of CryptoLocker from the same person or people that brought us the Australian Electric Company Bill version earlier this week. This time the author spent much more time on improving his product than they did on the delivery presentation.
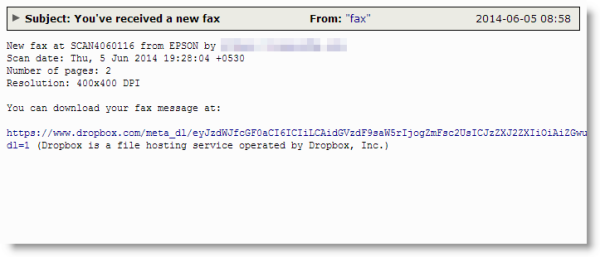
This one begins as a very simple plain text email pretending to be an email delivered fax as seen below. I'd like to point out that in an effort to evade filters or at least make blocking these a bit harder, the cyber thief has been utilizing DropBox links to give to potential victims. Much like many campaigns in the past, other virus campaigns have attempted to utilize legitmate, especially free, services to hide their malware. GoogleDocs was a favorite of spammers to peddle their pharma campaigns, but Google was usually pretty quick to clean those up. In this instance it would appear that DropBox does not scan their stored files for malware and CryptoLocker is taking full advantage of this. Hopefully they can join us in the fight very soon.
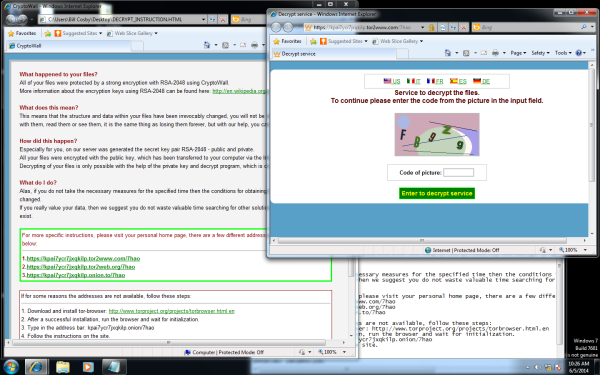
This one also appears to work a little different in a few ways beneath the hood though. Once the victim machine is infected, a few new pages pop up to inform the new victim that they have been infected. Three in fact, one is a webpage explaining what just happened. Another is a text file that expllains what you must do in order to decrypt your files entitled "DECRYPT_INSTRUCTION". An interesting note in the decryption instructions this time is that they include Tor links that are supposed to be "your personal home page". If you follow them though, you will just end up at a page that looks like the original instruction page that pops up when you are first notified of your new infection
The third page that pops up is reminiscent of the original CryptoLocker wherein it gives a little countdown timer. Originally this time was the time you had before they would destroy your personal encryption key, this time it states that when it runs out you will be charged double for their not so friendly decryption services. This go around it's $500usd/euro and then $1000usd/euro after the timer expires which appears to begin at 120 hours. Last go around the payments were accepted through Western Union or Moneygram, this time they're back to Bitcoin, and only Bitcoin this time.
For more information, check out the full article here: http://blogs.appriver.com/Blog/bid/102886/Faux-Faxes-Carry-New-CryptoLocker
The 5 Ways Hacker Malware Can Get Into Your Computer Systems and What You Can Do About It