I recently stumbled across an article describing data loss horror stories from 2011. The most disastrous occurrence described a server being struck by lightning, subsequently set on fire, and incurring water damage from the fire department’s attempt to extinguish the fire. Amazingly, the provider was able to recover all of the data from the charred servers because the company had their data backed up through a cloud service as part of their disaster recovery. Unfortunately, not everyone has a back up recovery plan or is subscribed to a cloud provider who can restore data after such a detrimental disaster. Choosing the right provider who offers the right services is a matter of patience, rationale, meticulousness, and a little bit of common sense.

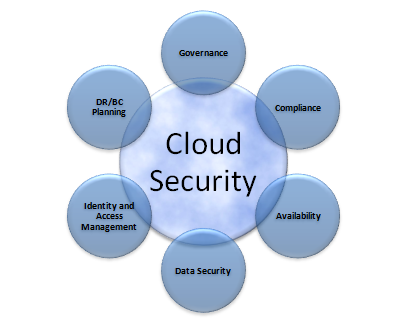
 On March 1, 2012, Massachusetts General Law Chapter 93H and its new regulations 201 CMR 17.00 final procedure went into effect – the provision of which included 3rd party vendors.
On March 1, 2012, Massachusetts General Law Chapter 93H and its new regulations 201 CMR 17.00 final procedure went into effect – the provision of which included 3rd party vendors. It can take new IT consultants anywhere from a couple of weeks to over a month to acclimate themselves to NSK Inc’s work style, ethic, and load. NSK’s newest team member, Ahmed Fadili, didn’t need such a substantial time period to become oriented. In fact, Ahmed was on site with a client during his very first days on the job. Determination and experience like this can be hard to come by and since February 6th, NSK has felt lucky and excited to have Ahmed spearheading the charge to find solutions to any technical problems encountered by clients on a daily basis.
It can take new IT consultants anywhere from a couple of weeks to over a month to acclimate themselves to NSK Inc’s work style, ethic, and load. NSK’s newest team member, Ahmed Fadili, didn’t need such a substantial time period to become oriented. In fact, Ahmed was on site with a client during his very first days on the job. Determination and experience like this can be hard to come by and since February 6th, NSK has felt lucky and excited to have Ahmed spearheading the charge to find solutions to any technical problems encountered by clients on a daily basis.