The following is an excerpted from an important blog by AppRiver on a new and highly dangerous Malware campaign

The following is an excerpted from an important blog by AppRiver on a new and highly dangerous Malware campaign
Topics: Disaster Recovery, Data Security
 Imagine if your business was suddenly hit by a virus or natural disaster that wiped out your entire server, data center and software programs resulting in the worst possible outcome: you lose all of your data. You and your employees no longer have access to your important documents that are crucial to running the daily activities of your business. In the blink of an eye, your business is wiped out. What would you do then?
Imagine if your business was suddenly hit by a virus or natural disaster that wiped out your entire server, data center and software programs resulting in the worst possible outcome: you lose all of your data. You and your employees no longer have access to your important documents that are crucial to running the daily activities of your business. In the blink of an eye, your business is wiped out. What would you do then?
Topics: Disaster Recovery, Data Security
Apple’s keynote at this year’s Worldwide Developers Conference confirmed (as if it were really ever in doubt) their spot at the top of tech. CEO Tim Cook spoke first, followed by Senior Vice President of Software Engineering Craig Federighi and his eighty-minute presentation of attractions packed into the coming OS X 10.10 Yosemite and iOS 8. There’s improved operating system aesthetics, huge application updates, and something they call “Continuity”. The first two of those are nice, improve on an already-nice, industry-leading product, but the third part is a big deal. Continuity is Apple’s push for complete and seamless integration of OSX and iOS, of its desktop and mobile platforms. With Continuity, you can search Safari on your desktop and pick up the search exactly where you left it with your iPhone with a feature called handoff; with iCloud Drive, you can easily work on projects, be sure any project-edits will save and hold across platforms, pick up on them whenever, and you can organize the cloud space however you like; Continuity allows you to pass a call from your iPhone to your computer. Working on one is working on the other.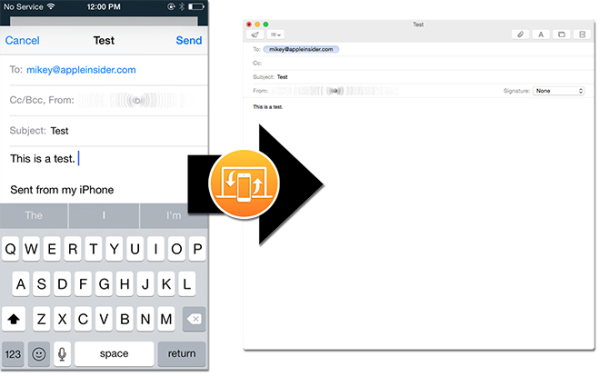
Topics: Cloud Computing, Managed Services, New Technology
 I know I’ve covered using passphrases in the past, but it warrants touching on again. The two most important aspects of a “password” are length and randomness. The amount of entropy (basically, uncertainty) is a function of length and randomness. For a brief discussion on entropy in cryptanalysis, click on entropy and scroll down about half way.
I know I’ve covered using passphrases in the past, but it warrants touching on again. The two most important aspects of a “password” are length and randomness. The amount of entropy (basically, uncertainty) is a function of length and randomness. For a brief discussion on entropy in cryptanalysis, click on entropy and scroll down about half way.
Topics: Data Security, Tech Fixes
You’ve likely heard something about net neutrality at some point in the past few weeks; if not, it is, simply, the concept that all Internet traffic should be treated equally, that no one entity, however large or small, should have more or less access to data transfer than another. This is so intrinsic to the way we expect the Internet to work that it’s difficult to imagine the opposite, an Internet in which data transfer speed – Internet speed – is bought into instead of de facto had. Imagine that a favorite site, ran by an entity of lesser, say, economic stature, is many times slower, takes many more seconds just to load than a site ran by an economically superior entity. Imagine that your favorite political blog, written by an intelligent, responsible person from their desk, has to match what Huffington Post pays to have their data load just as quickly. Of course, the favorite blogger could never compete with this buy-in “fast lane”, as it’s been called. This, a version of non-neutral net, is what the FCC’s new regulations would institute, and it’s going to dramatically change the way the Internet works. As Lawrence Lessig and Robert W. McChesney, co-founders of the media reform group Free Press, describe in their 2006 (yup, this has been around for a while) Washington Post article “No Tolls on the Internet”:
Without net neutrality, the Internet would start to look like cable TV. A handful of massive companies would control access and distribution of content, deciding what you get to see and how much it costs. Major industries such as health care, finance, retailing and gambling would face huge tariffs for fast, secure Internet use—all subject to discriminatory and exclusive deal making with telephone and cable giants.[1]
Topics: New Technology, Data Security