Business Protection Checklist
 Every business has critical data and applications they need to protect – personal work stored on laptops, business applications running on servers, or infrastructure systems like email and payroll. All of this information is vital to the operation of any business.
Every business has critical data and applications they need to protect – personal work stored on laptops, business applications running on servers, or infrastructure systems like email and payroll. All of this information is vital to the operation of any business.
If you are a small or medium-sized business, looking after all this data is a major challenge. You have limited budgets and limited IT resources. Let’s face it, sometimes things go wrong. Laptops get stolen. Email servers fail. Someone accidentally deletes a file, or even worse, an entire folder of vital business information. Systems get hacked, files get corrupted, and as we all know, disasters like fire, hurricanes and floods do happen.
BACK-UP DISASTER RECOVERY CHECKLIST
YES NO Are your laptops and desktops protected automatically?
YES NO Is a copy of your data moved off site each day, safe from fire flood, or sabotage?
YES NO Can you backup Microsoft, Linux and Mac?
YES NO Can you get your business back up and running in 15 minutes or less when a server fails?
Can you quickly viertualize your servers and work off the cloud
iof your business site is damaged?
Can you do all of this without spending upfront costs
on new hardware or software? YES NO
If you answered NO to any of these questions, your data IS AT RISK!


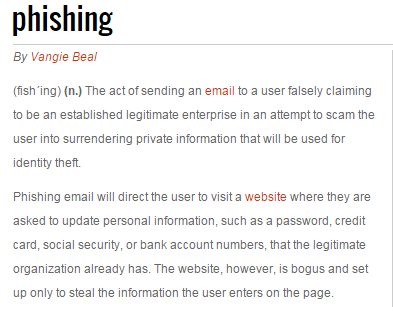
 If spyware was just adware and tracking cookies, it would just be annoying. But spyware has worse forms. Some spyware can change your computer settings, slowing down internet connections and slowing down your home page. Webroot SecureAnywhere Antivirus insulates you from these spyware attempts to infect your PCs.
If spyware was just adware and tracking cookies, it would just be annoying. But spyware has worse forms. Some spyware can change your computer settings, slowing down internet connections and slowing down your home page. Webroot SecureAnywhere Antivirus insulates you from these spyware attempts to infect your PCs. 

 Every business has critical data and applications they need to protect – personal work stored on laptops, business applications running on servers, or infrastructure systems like email and payroll. All of this information is vital to the operation of any business.
Every business has critical data and applications they need to protect – personal work stored on laptops, business applications running on servers, or infrastructure systems like email and payroll. All of this information is vital to the operation of any business.